External ExposureValidation
Your Most Sensitive Data Is a Target. If You Handle Source Code, PII, Financial, Health, or AI Training Data, One Exposure Is All It Takes.
Validate ExposureThe Defense Disconnect
While you manage security in silos, attackers see a complete map of interconnected vulnerabilities. These four stats reveal the gap between how you defend and how attackers operate.
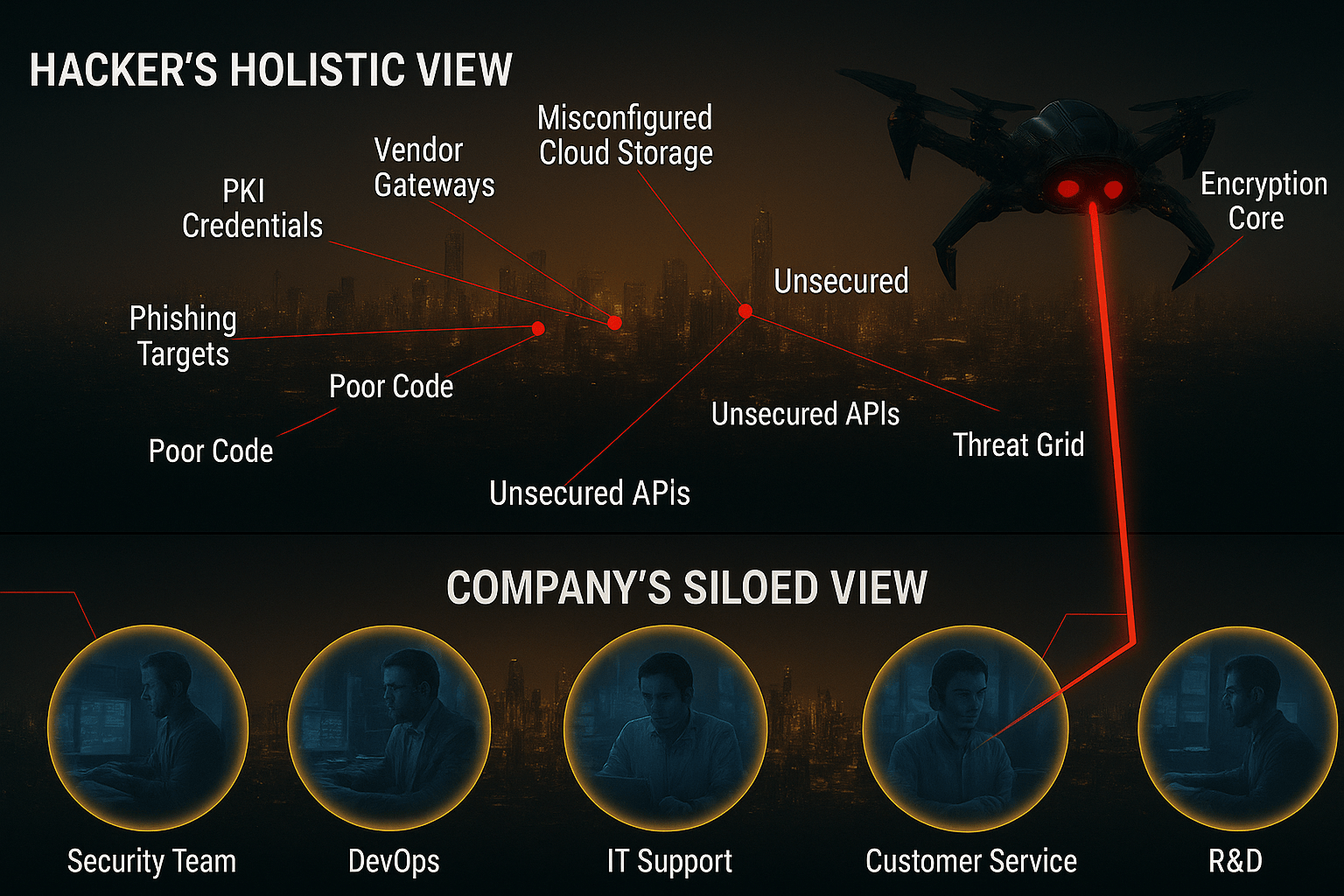


In today's enterprise, security is often managed in silos. Your cloud team, your IT help desk, and your development teams all have a piece of the puzzle, but no one sees the whole picture.
This creates a critical gap. You see compartmentalized problems; an attacker sees a holistic map of interconnected opportunities.
Preservers Advanced Cybersecurity Platform
Platform that understands your business context to keep your digital assets secured from external attacks.
Continuous External Threat Monitoring
24/7 monitoring of external threats targeting your digital infrastructure
Vulnerabilities in Context
Context-aware vulnerability assessment that understands your business environment
Supply Chain Intelligence
Protecting threats from your third-party vendors through comprehensive supply chain intelligence and monitoring
Benchmarking against Industry Peers
Benchmarking against your industry peers to identify vulnerabilities and improve your security posture
AI Agents for TPRM and False Positive Reduction
AI-powered agents for third-party risk management and automated threat response. Reduce false positives and improve threat detection accuracy
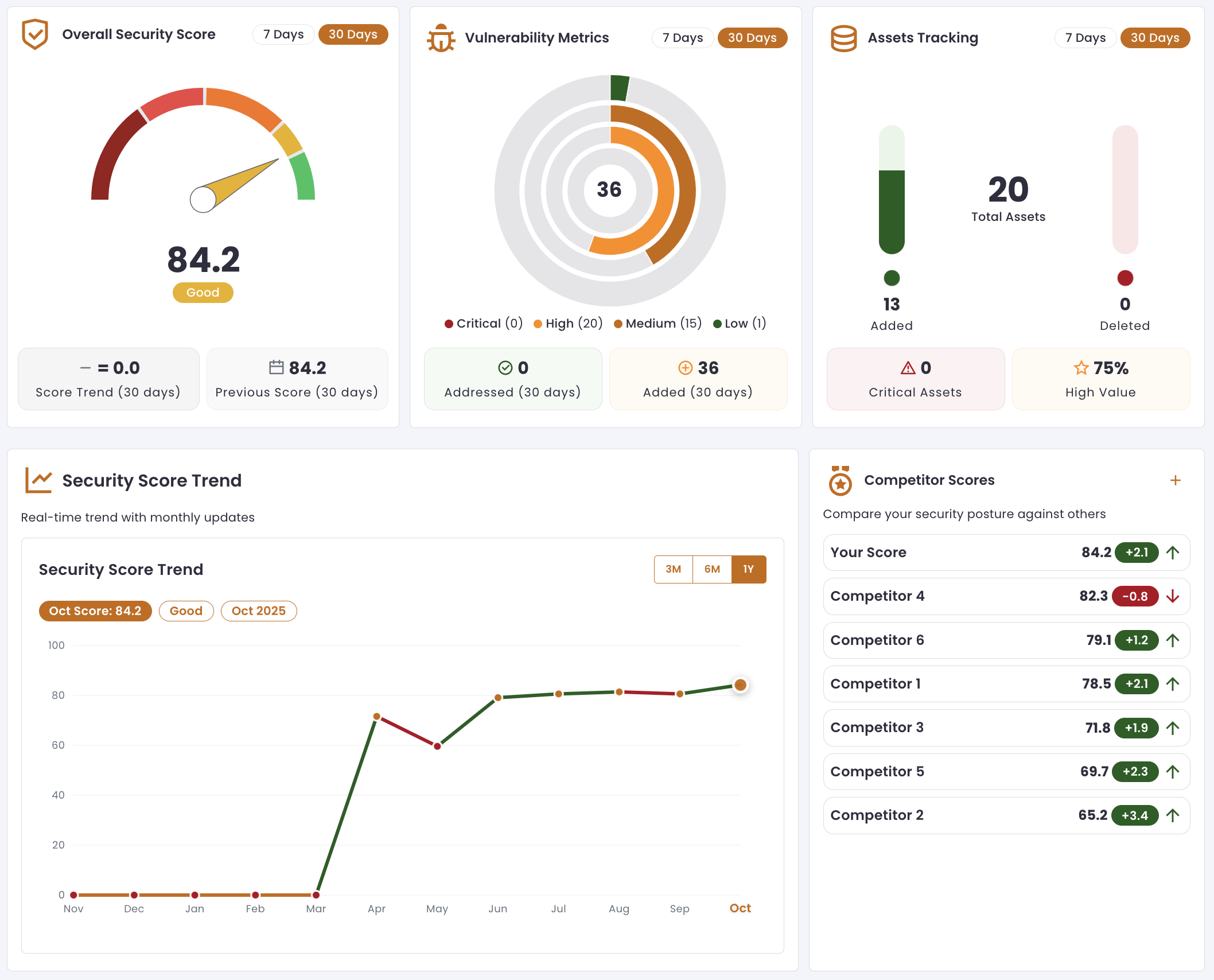
Advanced Threat Intelligence Dashboard
Real-time threat monitoring and analysis with AI-powered detection capabilities
A Paradigm Shift in Cyber Defense
Traditional security approaches are no longer sufficient against AI-augmented threats. The landscape has fundamentally shifted from human vs. human to machine vs. machine warfare.
Asset Discovery
Manual scans, known IP ranges, domain lists.
AI rapidly identifies "shadow IT," forgotten assets, and unknown subsidiaries by analyzing behavioral patterns across the web.
Vulnerability Analysis
Signature matching, CVE lookups.
Generative AI customizes exploits in real-time, bypassing known signatures and creating novel zero-day variations faster than security teams can patch.
Supply Chain
Static vendor risk assessments (point-in-time checks).
AI exploits runtime dependencies and complex third-party code interactions (e.g., malicious npm packages, compromised open-source projects).
Speed & Scale
Attacks measured in hours/days.
Machine vs. Machine Warfare. Attacks measured in minutes, overwhelming security teams with noise.
Recognized for Innovation
Building the future of cybersecurity with industry recognition and patented technology.
Nasscom Deeptech Club
Recognized by Nasscom Deeptech Club for our innovative approach to cybersecurity. We are part of a select cohort of deep tech startups driving cutting-edge solutions in India.
Pending Patent in India
Our core technology is under patent review in India, protecting the innovative methods that power our predictive defense and attack surface intelligence platform.
From Reactive Compliance to Predictive Defense
A unified platform that anticipates and neutralizes threats before they materialize.
Why Preservers Stands Apart
Dynamic Discovery
Finds what an AI attacker would find through behavioral analysis, not just static scans
Predictive Risk Scoring
Based on live exploitability and asset value, not outdated CVE scores
AI-Curated Alerts
Low volume, high fidelity alerts to prevent security team fatigue
Deep Supply Chain Focus
Monitors every single dependency, not just surface-level vendor assessments
Intelligent Task Automation
Agents that handle routine security tasks, freeing your team for strategic work
Compliance in Check
Continuous monitoring and reporting for regulatory adherence, so you stay audit-ready